UPDATED: https://www.marcelvarallo.com/?p=1497&preview=true
If you’re inclined to hardware hackery, see my recent post.
If you’ve recently acquired NBN broadband in Australia you’ve probably been given an Archer VR1600v router to go with it. A free router is great and all but sometimes you feel the need to fix what aint broke and voiding the warranty is the only way to scratch that itch. Fortunately, root (or more precisely super user) credentials are real easy to find out in this case so read on…
- First things first, open up chrome and login to the router.
- Navigate to the Advanced tab and then the USB Sharing menu.
- Open chromes page inspector tool by right clicking somewhere on the page and clicking “inspect”.
- Next click on the USB Storage Device menu item on the left there.
- In the Inspector Tool click on the Network tab across the top and you should see a list of pages and CGI items listed.
- See that one labeled CGI followed by a bunch of 5’s ? Select that one and you should see the contents pop up in the right hand column. Now scroll down and there it is.
- The SU (super user) username and right below it is the password. See my example image below if you’re lost.
Now go break some stuff!


very clever and helpful solution marcel, thank you
Do you use SU access through webpage or telnet etc ? Mine shows no user names enabled and no names/passwords apart from admin/admin in the USB page inspection.
thanks for the info, pwd and build update, just got v2, flashed, su login works fine, thanks again
ahem, a dumb question:
I have a (new to me) v2 Archer, flashed from iRishness’ link here the Archer_VR1600vV2_0.1.0_0.9.1_up_boot(200304)_2020-03-05_16.44.11.bin, can log as su, all good
now, did a factory reset on my v2, oops, su password doesn’t work anymore…
re-flashed above .bin, still su pwd doesn’t work..
BUT, loging with admin, I can see telephony menu OK..?
so… I now have su access with admin ? or, did I screw up something and, lack understanding?
just re reading iRishness’ post…
but, before I factory reset, su loging worked..
so, I guess all I lost is ‘su’ user/password …?
you shouldn’t have updated the firmware if you already had a version allowing su access, not a big deal as you do have access to the menu’s just using admin login which you previously had through su
thanks!
I just bought that v2 unit, only had standard login access;
flashed f/w from your link, was able to login as su
but, as the unit had settings from previous user, I thought I should factory reset prior to use – as far as I could tell, user settings survived f/w flash – after reset, su didn’t login, so re flashed
I’ll re check what file I’ve flashed originally, I’m not there now
originally, unit was: 0.1.0 0.9.1 v5006.0 build 200810 rel 53181n
flashed to: 0.1.0 0.9.1 v5006.0 build 200304 rel 64006n
anyhow, it’s working fine with Tangerine and Crazytel, I just hope snmp on this v2 works better than on v1
“originally, unit was: 0.1.0 0.9.1 v5006.0 build 200810 rel 53181n
flashed to: 0.1.0 0.9.1 v5006.0 build 200304 rel 64006n”
the firmware you flashed from should not have had su access as this version was flashed by TPG to update the su password so it’s weird if you had the password (out of interest what password were you using?)
the version you have flashed to gives access to the menus previously only available with su login so nothing to worry about
G’Day Marcel,
I have two of these dreaded TPG versions of the TP-Link Archer VR1600v Rev2.0 Routers, both locked and rendered basically useless by the establishment of the Super User Account and the hidden password.
TPG seemed unable to properly establish the VOIP account. I could ring out but no one could ring in. A long standing problem so it seems! It could be due to a router setting or possibly a lack of bandwith on the sideband assigned to the VOIP channel. After some 20plus hours on my wife’s mobile and plenty of promises to fix the issue… no change. So I changed……. to a better ISP.
So I have two of these routers. My current ISP suggests I should introduce them to a 4lb hammer and then place them carefully into the electronic waste at the council tip as their people have tried, unsuccessfully, to break them out of the TPG death grip. I have been unable to find a 3rd party firmware flash that could return the routers to use as none of the ones I have looked into say they are compatible with this particular device. I am reluctant to add to the electronic waste issue if these devices can be recovered and put to better use.
Any ideas?
Regards,
IC
so this is a version of firmware [Version:0.1.0 0.9.1 v5006.0 Build 200304 Rel.64006n] which if you flash to any V2 device will give you access to the Telephony (VOIP) and other menus CWMP etc [ https://drive.google.com/file/d/101owX9UXWxqPT950kTLntBNuPZxAWbGd/view?usp=sharing ]
so you should have a fully functional device note the superuser password is not known for this version but is not required to access the menus just login as admin admin
Hey @Irishness, that’s very useful but can’t TPG just force flash back over the top, if we can’t disable CWMP?
Would it re-enable VPN?
like I said you have access to the CWMP menu with this firmware so just disable it so TPG can’t force flash another firmware to the device. I assume the VPN menu (as I believe this version of firmware unlocks all the hidden menus) is available but don’t have it running to be able to confirm.
Wow! Thanks heaps. Gonna set up always on VPN!
Thats fantastic thanks but I have firmware version 0.1.0 0.9.1 v5006.0 Build 200810 Rel.53181n which I am led to believe is the latest
Can I flash this one over the top if its older?
Does you know if we can get TPG to flash back their firmware if we have troubles with this firmware? Cheers
I just installed this firmware over 0.1.0 0.9.1 v5006.0 Build 200810 Rel.53181 and it works perfectly. Voip credentials visible. CWMP turned off in the advanced system tools menu. Hooray! Big thanks to Marcel and the community.
Thanks see my comment below I did the same but getting internal error popups
So I installed the firmware and gives me super user to my admin login awesome!
Just noticed though on some screens I get an Error Code 1 Internal Error popup.
Once I dismiss it, I need to refresh page and it seems to function ok and can make changes
Anyone else have this? I downgraded when I installed this custom firmware so I am worried thats broken something? I was on the latest TPG firmware of 0.1.0 0.9.1 v5006.0 Build 200810 Rel.53181n
Thanks
It doesn’t really matter what version of firmware you run (I have used a V1 running old firmware without issue), the later updates from my understanding were to update the superuser password and actually remove some other functions from users. TPG etc don’t want users fiddling with settings because it causes them more work with tech help when things go wrong. People assume the latest firmware brings added benefits but this device has had stable firmware for a long time.
As for the errors you were seeing I can’t comment as I’m not with TPG or the likes and I’m not running this firmware on my main device I just flashed a backup device
The SU password (posted around Jan 2020) no longer works, but this method did the trick – big thanks!
This has meant that I’ve been able to set up VOIP with a new ISP (moved from Internode to Spintel).
Thanks again!
Thanks for this bro. I flashed it and the piece of garbage still forced the TPG settings with no changes.
Did a factory reset and BOOM. Auto-detected MyRepublic settings.
I had a similar problem with a replacement Archer VR1600v received from TPG. Only found out by chance that while we could call out we were not able to receive calls.
The router was preset to another person and different telephone number! The TPG help tried several times to fix the problem but the fix did not hold and it kept reverting to wrong ID. Using the previous information (SUser) I was able to make changes that held up to now.
All this happened about 12-18 months ago and not sure of the specific process I used but was able to find the preset info name and phone number, (located in Ringwood while I am in Carnegie).
Apart from this glitch am happy with the Archer.
Perhaps this info may help.
Hi Marcel,
I also have one of these nasty locked down, but probably open to any scammer, TPG TP-Link VR1600v Rev2.0 routers (actually 2 of them). I cannot find anything useful on the TP-Link website about this piece of kit and as yet I haven’t found any jailbreak software that says it works with this device. The problem has been described many times before:- VOIP hidden, CWMP no doubt open to the world, and SU password hidden. My current ISP, having ditched TPG because of their poor support, suggests I bury a 4lb hammer in the middle of the router and then consign it to the electronic waste bin at the local tip. I dislike the concept of filling up the world with discarded electronica and would like to re-purpose this thing so I can use it as an NBN router with VOIP. Anyone know how to access the Super User account? Tried all the posted methods, none worked>
No longer works, TPG have encrypted the password somehow, it shows as “*****”. The modem would be passing that password around, but they must’ve change the firmware. TPG are supplying new Internode/iinet/TPG customers with the crippled TPLink modem, with hideen VOIP details and a public facing Superuser password to allow them to unlock at will. I suggest anyone who wants to BYO modem or is concerned about security & privacy go with another ISP, maybe AB is a better choice. They are what Internode used to be, before they were taken over by that TPG behemoth.
That is the case with me as well. Has someone found the solution. Please share.
Security by obscurity is not security at all.
TPG are negligent in allowing a Superuser password on your home gateway modem!
This is a big security hole and the reason we got a TPG bill for $2000 of international phone calls to Senagal. TPG played dumb and pretended they didn’t kow how this could happen, but we traced IP addresses to overseas, so obviously not us. TPG users don’t have access to SIP login details, so no way they could call from Senagal. Internode used to give out SIP details and we could use them on a mobile SIP app, but TPG made the stupid decision of hiding them in the modem, and allowing the whole world to access them with a Superuser password. This is negligent and the ACCC need to investigate such behaviour from TPG. The reason the superuser password is enabled is to allow TPG to remote login and diagnose and update, notwithstanding the security risk it creates for its customers.
Any of this still work? Anyway to load the original firmware from TPlink that still has VPN capability?
I’ve since ditched the node and gone over to Aussie broadband.
My only problem now is, what should I do with the old TP-link? I don’t want it ending up in landfill.
Um. Be alarmed and alert.
I HIGHLY recommend you turn off CWMP
Just had a little search and not only does this page show the Username and Password in plaintext – the URL is http, path and port are hard coded. So, I am no hacker – but to me this would suggest you could write a small program to parse TPG ranges and then login over http. Yes I tested it. I am gobsmacked. Will reach out to our host on Telegram. Far out.
I tried to do your suggestion but the su password for the Archer V2 as of Today doesn’t work for me, I fear the my ISP pushed a new firmware out and the password got changed, can anyone else confirm or get the updated one?
Unfortunately I only have the V1 so I can’t help further.
Marcel, thanks for this post and the great discussion in the comments, most helpful when I found my VR1600V (v2) had been screwed with, b0rking my VOIP 🙂
You want my v2 to mess about with? It’s yours! eMail me and we’ll figure something out…
@BC, did you figure out the PW for the new V2 update?
Sadly, no. I’ve given up.
It needs someone with far greater patience and skills than I possess 🙂
You’re not located in Melbourne by any chance are you?
I am! Glen Eira area.
Happy to post to you, if you want the hardware and meeting up is too tricky. 🙂
Hey Marcel, which tool are you using to extract/dump the firmware from the router?
I have a v2 device, so I can have a crack at it.
Cheers
They did unfortunately. Build 200810 Rel.53181n Hardware Version:Archer VR1600v v2 00000000
Yeah mine doesn’t appear to be updated yet. Will let ya know the moment I can get an update.
I can confirm also – Dec 2020, it’s omitted by “*****” now.
Firmware Version:0.1.0 0.9.1 v5006.0 Build 200810 Rel.53181n Hardware Version:Archer VR1600v v2 00000000
I did have su access until I had a problem yesterday with my NBN and re-enabled CWMP (big mistake!) and then they (iiNet/TPG) updated my firmware!
I am keen to uncover the new su password changed as part of the latest firmware update which is now:
Firmware Version: 0.1.0 0.9.1 v5006.0 Build 200810 Rel.53181n
Hardware Version: Archer VR1600v v2 00000000
I assumed you used V1 hardware to uncover the password initially?
Did you use the 4 pads on the circuit board to monitor traffic? Is this a serial interface?
Are you able to share the method you used? I am keen to assist.
Some silly people online post it in the TPG forum – that’s why it’s patched possibly!
https://community.tpg.com.au/t5/Modems-and-Devices/Archer-VR1600v-v2-Super-User/td-p/79436
I can confirm yes they’ve changed the password
I need to change the telephone number stored in my Archer TP-Link VR1600v V 2.0 Modem/Router.
I Received it as a replacement from iiNet for the original TG789 vac Modem/Router, which failed after 18 MThs. Initially the TP-Link appeared to be working OK. But then we discovered that we could not call home using our land line number.
Checking the settings discovered that the modem may be recycled. It has user ID and telephone number that don’t belong to me. Called iiNet service and second person was able to change the number and restore the upload speed which was only 0.75 Mbps I did not believe such a low speed could work, but it explained why some sites would not load sometimes. I just assumed the web was busy.
To explain further about the telephone. We could make calls and even received calls but these either did not respond to our greeting or were in Asian language. So we assumed they were spam or junk.
Once I used dialled the number in the router, our house phone rang. Using our telephone number we got a message “Phone not connected” and an error code.
Several days after the ‘Fix’ the telephone reverted to the wrong number. Calls to service have been useless and problem still here.
I found this site and used Su and Pwd. and have reached the area where Phone number are stored and tried the Edit function but still can’t change the number. Can you/anyone help please.
I’m having trouble with FTP on my TPG VR1600v v2. I’ve checked just about everything to no success – different computer, disable firewalls, phone TPG et al.
A friend also has TPG FTTC NBN with a VR1600v v2 and their setup is OK with FTP.
Unfortunately, I can’t get their su password as the listing as described here only shows ‘**’ as the admin username, and ‘*********’ as the admin password.
The password which works on my VR1600 doesn’t work on the other one.
I need the su password so I can backup the other VR1600 before changing anything to try my VR1600 at a different location to prove or disprove my theory that it’s my VR1600 that’s not working correctly on FTP, and the other one works OK at my home with my configuration.
Try su and VExy!64a3ng
Many many thanks Marcel – that password worked fine.
Now all I have to do is continue my investigations.
Regards,
Darrell H
Hi all
I have just come across this post/thread after tried to find why my Archer VR1600v1 reset itself to factory settings about 3 weeks ago.
I noticed this issue on the Whirlpool TPG form section as well.
But’s not just TPG. I’m with Internode and noticed this arvo my Archer VR1600v1 had reset itself, back to defaults (including admin admin login/pw)! I was wondering why my custom login was failing as ‘incorrect’ when I wanted to login to make WiFi adjustments. After much frustration, because I knew my ID and Password were correct, I just tried the default factory login… and it worked.
My previous WiFi settings were defaulted. My WiFi schedule settings were gone, my Dynamic DNS ‘No-IP’ details were gone.
My custom login details were still displayed but didn’t work. I had to use the admin admin to change it back to my custom login again. I can’t find anywhere in the system tools log history where and when this occurred. Any help to find? I don’t use my router for VOIP, so don’t know how this could have possibly happened? There were no power outages and even so this should not cause this to happen to this modem. Never has before.
Also ever since then my ProtonVPN killswitch kicks in when using QBittorrent (also UTorrent) with UDP/utp connection protocol. The only way to get a connection again was to reboot the modem, restart ProtonVPN and QBittorrent.
I called Internode and they said they don’t block P2P activity and I wasn’t using the ports they do block, so they siad the issue is not with them. I had already tried ProtonVPN support and they said the issue was not a fault caused by their VPN. My Bitdefender Total Security support said it was not caused by their application as I had permitted all these applications access through the Bitdefender firewall.
After reading this post and a few others I am thinking it is likely to do with the modem reset and Internode/TPG have screwed something up? I am on NBN FTTC connection.
I have now used the Super User login to disable the routers CWMP settings. Do I (or must I) perform a ‘reset to factory default’ to fix any tampering from the ISP or is a simple reboot sufficient?
Maybe I should just ditch the ISP Archer modem and dig out my old trusty FritzBox 7490 router I used before getting NBN connected?
Any thoughts or advice would be greatly appreciated?
I still had the problem after using the Super User P/W to disable CWMP, reset the modem back to factory default, then re-added my custom settings.
In the end I ditched the Internode/TPG Archer modem and went back to my old FritzBox 7490 router that I used pre-NBN connection. That instantly fixed the issue and haven’t had any disconnects since. Would recommend using a TPG/Internode supplied router unless you want them to be covertly interfering with it.
Meant to say
**WOULD’NT recommend using a TPG/Internode supplied route**
Ok, so we’re able to get into the full functionality of the router now. Does anybody know if it is possible to change the su password? It really would be great if we could stop Internode/iiNet/TPG from getting back into our router and messing things up.
Yes Peter B, this is a good point. I guess it must be possible as it a programmable device. Legally changing it may also depend on whether the router has been bought of the ISP or if they still own it and the user is ‘renting’ it as part of the fee-for-service?
Either way I would like to know and change it if possible.
TPG called and instructed me to change the remote access port from 80/443 to something in the range of 30000-40000. When I ask him why port 80/443 are blocked he advised they are still investigating haha, will the truth ever be revealed ?
So I’ve just come across this page after having my V2 reset to factory defaults sometime after midnight on July 1. I’m not alone a few others reported the same issue occurring at the same time
Others also reported fraudulent VoIP calls made on their account at the same time.
Now because of this my suspicions of our devices being hacked seem plausible. With this su login it seems devices opened up to remote management enabled would have had their VOIP credentials exposed and all of us would have been vulnerable to CWMP since the superuser login exposes the same user name and password to access every device on the network. This explains how our devices got factory reset
Now the question is how did they get in? Is CWMP only accessible from within TPGS network or can it be accessed from as anywhere if you know the IP address
TPG keep deleting any post made about this incident on their community forum (suspicious!) But I’ve also posted on Whirlpool about it. TPG are remaining very quiet about and blaming a power outage for the factory reset! Yes seems every affected TPG user had a power outage at the exact same time causing a factory reset which wouldn’t cause this to happen in the first place!
You guys already called it earlier that we were vulnerable. Seems something probably happened. I’ve disabled CWMP now. Remote Management was always disabled. I hope this protects me but I know I’ll have to reenable it if TPG push out a new firmware to plug the hole. Which at this stage would have to be a new firmware with a new su password and make sure this password is not exposed in the network inspection! How amateur in the first place!
Very interesting! I was one of the unlucky ones that had over $300 worth of VoIP calls made to Manila & Hong Kong. Makes me wonder if TPG servers were hacked as my modem had remote management disabled as I never needed it! So, I’m really confused as to how the modem was hacked if that was disabled as TPG has said it was due to this setting that users with VoIP calls were compromised.
That’s interesting. I had remote management disabled as well but never had unauthorised VoIP calls. I figured the only way hackers could gain access to the VoIP credentials would have been to login the UI with the super user account but with remote management disabled on yours obviously this was not the case
All users howevee including myself were vulnerable to remote configuration being pushed to the device using CWMP which can only be disabled using super user. Any users logging in with superuser can view the standard connection details used to remotely configure the modem including the credentials so this is how the factory reset was sent. Maybe using this the hackers were able to push a change to make remote management enabled so they could login and get VoIP details? If so I was lucky I only got a factory reset done
Great article, very helpful. I’m now able to use my modem with my new provider. Thank you very much.
Thanks guys! IP phone working with iiNet now.
V2
User: su
Pass: VExy!64a3ng
Thanks! Exactly what I needed. Followed the instructions above but su is now shown as **** in the inspect page. So needed your answer. Thanks for posting.
Thank-you! Also only had * following the above instructions.
iiNet/TPG modem.
Anyone have any luck getting rid of the TPG firmware and replacing it with anything else more sane?
I have 3 Archer vr1600v v1 in my house and they won’t stop sending them to me, I just wanted to put one in wireless bridging mode to make an access point/extender but for some reason TPG remove that functionality
Marcelo password work last month, But now the admin (user and password) are now masked by **********. Does anyone have another way we can view the password.
Cheers
Dan
Thanks for providing the su password for V2 and unlocking the Telephony settings.
Seems like WDS is still missing though unfortunately.
Hi Marcel,
I have a TAIPAN AC3200 Modem instead of the tag standard unit. Got the Internet working NBN but when hooked up landline phone was dead silent. Rang TPG and they are saying this is only allowed with their modem. Reading the posts am I able to configure this modem myself with the SIP settings?
Thanks for posting!
Not sure if this is known, but after getting my su password, I noticed “cgi?8&8&1&1&1&1&1&5” contains the telnet username/pass with works on port 2323.
Still not able to get a shell, but there’s some debug in there perhaps someone smarter than I can make use of?
edit, forget me – the exact same info is indeed in the update link.
I’ll go back to trying some of the httpd cve’s against the box …
Confirmed VR1600v2 super user login worked.
Thanks for your help, absolute legend!
I tried this method with the same model router (ver 2.0) supplied by iiNet just a few weeks ago, and the results are shown in the screenshot at the address below. The adminName and adminPwd values are shown as stars. Marcel, how did you get Chrome to display those values in plain text? Or maybe it can no longer be done because TP-Link has changed the firmware since you did it in March to prevent others doing the same? See screenshot at:
http://moongazer.zeriha.com/website/files/Archer-Chrome-Inspector.jpg
The password is published here on the forum.
Look up the thread from Marcel on 8th January 2020.
Hey Guys,
Just so you know the fight is not over yet, my local member of parliament is back her reply is as follows.
“As you note, this is a bigger issue. I will forward the information you provided to me in your email of 18 December to our Shadow Minister for Communications as a starting point. There are certainly some questions to be asked regarding privacy and security.
I will keep you posted on any advice I receive.”
I would like to compile a list of companies that are providing these modems and supply as much information as to just how compromised these modems are. So if any tech types want to give me some fuel please do.
Good quality information will give this thing wings.
Ok guys,
TPG are really playing the game here. I can only take the stand point that they are being deliberately evasive.
Here is the last msg from them to me.
I understand that you seek TPG to provide the root/master password for the TPG modem;however,as discussed by our Senior Engineer,we do not have it.As you may already know,our TPG supplied modem has been pre configured and has been tested by our network team to ensure that it meets TPG/NBN criteria for service stability.
Should you wish to change the admin username and password for added security,you may do so by accessing the GUI of your modem.However,I assure you that TPG is providing you a secured connection.
Given this situation,if you are not happy with the current level of service,you may look for another provider that can satisfy your needs,and TPG is willing to release you from contractual obligations as a gesture of goodwill.
Please take time to consider the information that I have presented and let me know how do you wish to proceed with your account.
How good of them to do so, please excuse me while I go take some fresh air.
Hey guys for those of you more knowledgeable than me.
Seeing as we have the SU for the V2 is the tplink we have a candidate for perhaps a home brew upgrade?
Get rid of TPLINK firmware totally?
If anyone has any links as to how we might be able to go about this would be appreciated.
Ok Guys n Gals,
After a few weeks of to and fro between Ombudsman and TPG.. TPG win, Ombudsman dept toothless tiger.. Have a read and laugh at the last mail from TPG to me… note that because the SU/Master user login is not mentioned in the user manual, it therefore doesn’t exist!!! There ya go, I spent a few weeks of my life to allegedly have this resolved by being sent a copy of the user manual.
Maybe its time to go to local member of parliament.
Someone here isn’t telling the truth.
——-
Note I have I have sent you the modem manual for you to know that there was nowhere in that manual where master password was stated. TPG therefore, is not providing nor supporting such feature.
Even if you escalate this further with the TIO, they will still refer you back to TPG. It is noteworthy to mentioned that TIO cannot compel providers to impose something not within their capacity.
At this stage, TPG cannot provide you the master password as we have no records of such. You may use the router provided without setting a master password or you may opt to seek for a different provide who can provide you the master password.
Well that’s complete bollocks and we know it. What user manual did they send you? Anything special or just one we would have seen before?
The password for the V2 modem was uncovered by one of our Telegram memebers.
I have tested password on a ArcherV2 supplied by internode and westnet and both Su and supplied password work on the units.
Yeeha! Well done guys.
Mate how do we get our hands on it please!!!
Super well done finding something that cough cough doesn’t exist.
Well done.
Looking into it now for you. I have the method, but I’m asking permission to share. alternatively if you join the Telegram group you can scroll through and see where one of the guys details it.
hey mate
would you be able to share the password with me?
cheers
VExy!64a3ng
Just the standard user manual from the TPlink website.. Nothing special.
This was the response from Internode technical support who suggested I look at this. Pretty pointless if you ask me.
***Begin Quote***
Hi
This is what we have discussed about those feature you are looking with out TP-LINK Archer VR1600v modem, unfortunately Back up and Restore is not included on this modem though call blocking feature is available.
You link rely on this link: https://setuprouter.com/router/tp-link/archer-vr1600v/manual-2515.pdf
If you have other queries don’t hesitate to call us back here, or you can reply on this email thread
Thank you
***END QUOTE***
Makes you laugh.
These companies are almost like petrol stations they all seem to raise their prices at exactly the same time and price.
The answer you got is pretty much the same as TPG heres the manual lol..
Laughable
hey Marcel
can you provide the V2 Su password please?
VExy!64a3ng
actually, looking at that reply they’ve just said “Nah there isn’t one in the manual” But we didn’t ask about one being in the manual. We asked about the undocumented one that’s on the router.
Somewhat conversely, if you (or anyone) does manage to obtain it and change it, TPG may be liable for any damages caused to you as a result, since they are clearly expressing they have no knowledge of it, which is either incompetence or negligence I suppose.
Well that’s just waving a red flag at a bull now. 😀
Seriously, its standard security practice to change passwords every now and then, so as to prevent cyber attacks. My V2 Archer is legitimately set to DMZ, so only I could update the password I guess, but I can’t since I’m not given it in the first place. Since the (it seems) generic password is now available (as posted in another post above), all of TPG’s customers with this modem are now compromised, which could be a considerable number of residential users in a country, opening the country up to cyber attack en masse… or am I just whistling dixie?
Arguably, all of this crap is backdoored to hell by agencies with acronyms so it was never really safe to start off with. But yeah, sharing passwords across multiple bits of CPE means that once 1 customer is compromised, then all of them are. I liked it better when you could buy something (software or hardware) and you owned it, so nothing changed unless you made the change. vendors pushing out updates is the bane of my existance.
That was one of my arguments with the Ombudsman’s office, let me tell you that THEY DO NOT CARE.
It’s staffed by people who haven’t got a clue what a modem is, I asked one of the staffers there, and have you checked your modem, the reply was. Ohhh I don’t know anything about them my brother does it all for me.
So they are the people looking after our interests….
how safe do you feel……………..
After you use the superuser and PWD to access all of the settings, can the modem be made to work with other ISPs? IE, Aussie Broadband
with superuser access, can the update be made to proceed manually?
While I was in provisioning stage, moving from a very slow TPG ADSL service to Internode NBN, the supplied Archer which we’ve all been trying to argue has a SU password was able to be configured to use my old ADSL service, so based on that it would be safe to say the modem could be used on another service, however each modem is encoded to seek the credentials from the network. You would have to know your NBN credentials and service type and how it is connected and any particulars like VLANs used.
Well the issues isn’t so much anymore configuring the modem to user other providers, its been shown that it can be done.
The issue now is we have the SU login and pwd for the V2, but you can’t for now change the SU login and pwd its either hardcoded or a method for changing it hasn’t appeared as yet.
Your modem is still vulnerable..
Lots of unanswered questions here.
How much control do we have after entering the superuser password.
Can the password be changed?
Is there a way to download the firmware to the PC, so that it can be uploaded to the modem at a later stage?
Can I use the voip details from the archer on another modem, IE, a billion modem?
From what I understand, yes if you have voip details you can use another modem. One of the guys here has said as much in a previous thread.
ATM there is no way to change the SU login and pwd, no one has as yet found a way to do it. Though there have been threads on the web about users changing the SU login and pwd for other TPLINK modems which also have a back door using telnet.
Once you log into your modem with SU, you have pretty much full access to the modem, as a suggestion you should switch of CWMP which will/should prevent auto updates.
So far your modem it would be fair to say is totally unsecured due to the fact that you cannot change the SU.
The only way to currently secure it is to either 1 use it in bridge mode and have it live behind another modem or put it behind a firewall. There are plenty of articles on how to go about that on the web.
The thing that you need to check with your Billion, I used to have one of those prior to NBN is to check to make sure that it also doesn’t have a backdoor SU login pwd.
A college of mine has a Netgear voip modem and currently he is not getting a straight answer from Netgear if there is or isn’t one.
Thank you for this info.
and sorry for the newby questions.
Is there any way I can obtain the firmware binary file and download it to my desktop, or back up the existing firmware and configuration files?
For example, suppose an update to the firmware comes through where there are changes to the voip settings and the old settings don’t work any more.
All the internode help desk techies, at least, those who have been on the job for more than 4 years know all too well about the botched update that broke things for net gear users, and one even expressed concerns off the record that he felt very iffy about the update process given what happened with netgear.
Just as a by the by have gone to the Telco Ombudsman, TPG have been in contact their complaints resolution center. Spoke to someone today, they were going to call back I expected today which didn’t happen.
Lets see where this ends up, so far its a flat denial that an SU login pwd exists.. in actual fact they go so far as to not knowing what an SU login pwd is.. seriously…
Mind you conflict resolution center admit to not being technically apt, so need to consult with tech dept..
Its funny I just had a run in with TPG, I asked them directly to give me the SU login and PWD. They deny that they have any such login pwd details and said TPLINK would have it and try them.
I called and spoke to TPLINK Malaysia, they say there is no such thing as a superuser login/pwd and to check with TPG ping pong nice game they play.
I’ve reported it to the telco ombudsman they have taken up the case and TPG have 10 days in which to give me a better answer. Will let you all know.
TPG are in contravention of our privacy laws, by not disclosing which 3rd party if any has a backdoor login/pwd to our modems.
They don’t lease the modems to us they sell us a service and sell the modems.
That’s hilarious!!!! Please let us know what happens. I mean we have direct evidence that they have several backdoors in plus the Super user.
iinet (recently acquired by TPG) put the “security” reason forward for not disclosing such information, and I imagine that this will be the final analysis for anyone connecting to the NBN.
I don’t like to jump the gun here, however I have managed to extract my NBN VOIP ISP settings using the “Quick Setup” function which for the normal “admin” account is not visible until you unhide the CSS code.
Once you get the tab “Quick Setup” running, it sits along side “Basic” and “Advanced” up the top you can attempt to complete the setup and go along the way until you get to the VOIP part, low and behold, there you are, your VOIP settings are staring you in your face, in which you will take note of all your settings and VOIP password. Then cancel Quick Setup as you would have not had to make and changes, just view and reveal the information you need.
Using OsX I downloaded from the app store https://apps.apple.com/au/app/telephone/id406825478?mt=12
Punched in the settings I extracted from the modem and all working from my desktop now.
Any chance of more detail on how you un-hid the “Quick Setup” menu?
for those of us that are a bit slow 🙂
Is there any way to send me a message directly. We can’t have this information easily available. Just to add. I am using a V2 router with internode. Since TPG and internode are basically the same RSP in the back end, they utilise the same equipment.
Not sure…feel free to send me any contact details on throw-away: jj12348-123@yahoo.com
I’m not sure how to PM on this site
please send me the info also at aldospa@atrove.com
please send me the info also at aldospa@atrove.com
Will need to know how to switch off remote update to the router, else this CSS exploit will be removed I guess in the near future, and passwords changed, etc.
My latest post mentions some usernames for a service that enables updates from ISP. Disable port 7547 basically I think. Or turn off ACS or cwmp if I remember rightly
Luc can you help me extract my voip password on an archer v2 from iinet?
Luc,
Can you please help show me how to un hide the CSS code.
Cheers,
Aldo
Hi Aldo,
I won’t post information like this on a public forum.
If you and anyone else are interested in knowing more, I/we can be reached on the Telegram App (alternative to WhatsApp) install the app and then by clicking on the following link: https://t.me/joinchat/AAAAAFE8QbBEQ8MSLYsQdQ
Hope to contact you and Marcel there.
Cheers Luc.
Haha you guys. I’d love to be able to provide a better private channel but I’m not really geared towards that due to my low page hit count. Direct email to me is just my name (like the website) @ me dot com. But I also see all these comments obviously and if you don’t get a response on my email just ping me here and I’ll check me spam folder.
Hey Luc, just tried out telegram but can’t seem to post. No little box for me to type in. Chat permissions issue?
Yep, i also joined the telegram chat, but I cannot post… Please change the permissions so that we can actually talk to each other. hahaha… I have the v2 here and it’s on the verge of being cracked. Let’s work together on this thing!
Please access the new group via this link: https://t.me/joinchat/JPFABkdYTLY-ygl9i6OSJw
The other link was a misunderstanding of the functions of Telegram.
If you do happen the previous link, I have provided the link to the true group there too.
Thanks Luc – you’re an absolute legend! Your method worked and I was able to get access to the VoIP details – cheers!
(My approach had been to retrieve these details via the CWMP service, but your method is much simpler!)
Hi there.
With this new archer vr1600v firmware, I can still recover the quick setup menu, but there are no entries in the voip section, so you can no longer see your details.
We’ll just have to wait until Marcel gets a hold of a v2 device and let him work his magic. I hope the method he used on the v1 will work for v2 devices.
Out of respect for Marcel, I am not going to put the method that was used to obtain the password in a public forum.
btw: the firmware is a beta.
Marcel,
We wait eagerly to see if we can’t stick one to TPG for V2 archer.
I’ve got the v1 modem not v2 but seem to get the su info masked. When try to login with su/yg… Info you note above it doesn’t work. Anyone have a new pass or workaround? Trying to use modem with new provider. Tpg said wasn’t locked but VoIP wouldn’t work.
I’ve got the v1 modem not v2 but seem to get the su info masked. When try to login with su/yg… Info you note above it doesn’t work. Anyone have a new pass or workaround? Gp
Nothing yet unfortunately. I’ve still not managed to get my hands on the new version hardware or the firmware binary.
I have a Huawei HG659 that has finally bitten the dust and was sent a replacement Archer that was V1 so was able to get the su password but it didn’t have any SIP filled out, just called the provider ACS.
Any suggestions for trying to get the SIP details?
I might have an answer to that. There was a file containing all the sip info on my one. I’ll take a look when I get home.
I should clarify the sip file I saw had sip details for a few carriers in a heap of different countries. But yeah, when I get home from work I’ll find it.
My sincerest apologies for the super late reply. Does this txt file have what you need I sourced it from the archer java on the router. e.g.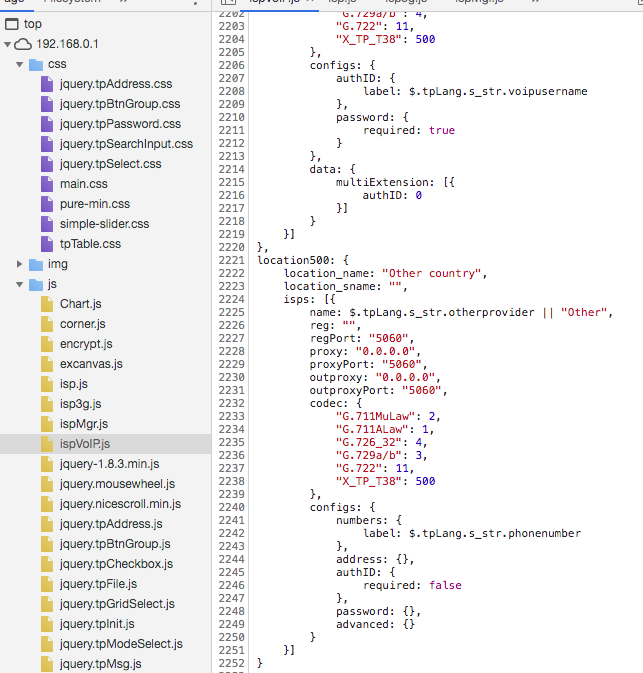
The problem with the new routers that they hand out is that the response is no longer showing the admin username and password. I’ve checked this with wireshark. Its not a browser issue about what version the browser is.
Many thanks to marcel.varallo and others here. I have a VR1600v V1 and the ‘su’ and password worked OK for me.
I was very pleased to see that it bought up the Telephony section – one part of which is, to me, quite important. The ability to block numbers.
I’ve been plagued by scam calls about the NBN being available and phone bein cut off. Now I can block those numbers.
Hooray !!
Awesome! Glad to have helped.
And thanks for coming back and leaving a commment 🙂 much appreciated.
I’ve had the same result with my V1.
Worked a treat to block those annoying callers. I never realised how vulnerable my archer was.
Hi Marcel and friends. Thank you for these postings.
I have just got the iiNet V2 of this modem, with firmware 0.1.0.0.9.1 v5006.0 build 190228 rel 72265n
Using both your method as well asa similar one with Firefox developer tools, I find that both the admin user and password are “starred-out”. User is 2 chars, so probably “su”, but the password is now longer (11 characters).
Any further info from you would be most appreciated. Cheers, Mick.
I wish I could get hold of a version 2 without having to hunt one down and buy it. I’m keeping an eye open and the moment I can get one I’ll update. But yeah it looks like you’re correct about that being su still. Even getting hold of the firmware file for it would be a massive help. Then I could binwalk it and find the password that way.
need root password for Archer VR1600v v2 did you manage to get it?
hate locked modems!
Not yet. If anyone can get me a firmware file I’ll binwalk it and see if I can work it from there.
I’m having trouble getting a console over the serial header. I’ve connected a buspirate to the port and i think i have tried every uart mode possible and cannot get anything. I have the v2, if anyone could point me in the right direction, that would be awesome. I need to extract my voip creds
Oh I like you. 🙂 That’s what I wanted to do. But sadly no router to try it out on yet.
Don’t suppose this txt file helps you?
Nope, I don’t think that will help unfortunately, but thanks. I’m also with TPG. I would give you my device, but then you might end up with my creds;) haha
Hi Marcel,
Did you ever manage to get the su password for the V2?
John.
Nothing yet I’m afraid. The moment I get my hands on one I’ll be posting some replies here to let you all know. If anyone snags the firmware for it let me know, but otherwise I’ll be prying it out of the hardware when I get my hands on it.
didnt work for me; Note password has 1 extra character
Firmware Version:0.1.0 0.9.1 v5006.0 Build 190228 Rel.72265n Hardware Version:Archer VR1600v v2 00000000
serverName=Archer_VR1600v
…
rootName=
rootPwd=
adminName=**
adminPwd=***********
userName=admin
userPwd=admin
[error]0
I’ll have another look this week and see if I can find it in the new build.
Obviously the first thing to do is disable remote route administration System Tools->CWMP Settings
Obviously the first thing to do is disable remote route administration System Tools->CWMP Settings
It’s appears that with the FW ver 1.0.0.9.1v5006 Build 190228 the method is no longer valid. Just lists ******* as the user and Trev
Would the nirsoft utility bulletpassview help with the stars perhaps .
I haven’t tried the program but seen it yesterday while browsing.
It’s open source freeware
I had the same thought, but it seems it’s masking junk data that’s acting purely as a placeholder. Good idea though. Eventually we’ll turn over the right rock and there’ll be some su creds hiding underneath.
Hey Marcel,
Im using Chrome 75 on Linux. With a “later” verion of Chrome the instruction have changed a bit
1. goto 192.168.1.1 and use admin/admin
2. Right click anywhere and inspect element
3. On the inspect Element navigate to network –> here is where it gets a bit different
4 Press CTL R to start recording
6. NOW… Navigate to Advanced then USB Sharing
7. Find the element that is NOT CGI with all the 5’s… its actually 5s and 1s
without the ampersands its CGI?55151155551
Lo and behold, I have the same su password as you > adminPwd=ygDT92!ez7
GRI2A
received Archer VR1600v V2 from TPG
tried your method but……
all my user name and passwords are all in ****** under chrome’s inspect page
could you please tell me how to make it display those infos ?
Hmm not sure why they’re masked out for you . Might be new firmware maybe. Try su and ygDT92!ez7 as the user and password.:P.
doesn’t work
I guess TPG blocked users with their new V2 router
what version is your router ?
TPG oh NO,
Ive got the latest VR1600v and the latest Chrome,
Have a look at my slightly updated instruction
GRI2A
TPG oh No,
Sorry, dont know what to say. On my broser it works fine.
I am however using Chrome V75.0.3770.90 (Official Build) (64-bit) on Linux… might have something to do with your Chrome version
GRI2A
This is great, so simple to do (once you know what to look for) are there any ways to enable the hidden features? there are many items that are not visible.
Wow! That’s what I needed to disable VoIP on my router. Thank you!
need to know Archer VR1600v v2 tag root password, did you manage to get it?
Both user and pass were blank when I looked but that could be a layer above the actual Linux backend. I’ll have a look at the same time I look for the su password on the new version. I’ve just moved house and been issued a new modem which may have the same issue as yours. What did you want to use root for? Maybe I can find another way?
Was the new Modem ver:2.0? I got mine the other day and same prob v2 and cant get su pwd. Having to have the old router with voip hooked up behind to keep my third party voip
Yeah, v2 is the one that people seem to be having trouble with now. I’ve not had a chance to get hold of one to take a crack yet. Will definitely post some replies here when I do